2024 AIS3 Pre-exam Write up
我這次只解出7題(含Welcome),真的是菜到不行,前陣子才練習pwn題,結果這次一題都沒解出來。
Misc: 4
Web: 2
Rev: 1
Crypto: 0
Pwn: 0
Misc
Welcome
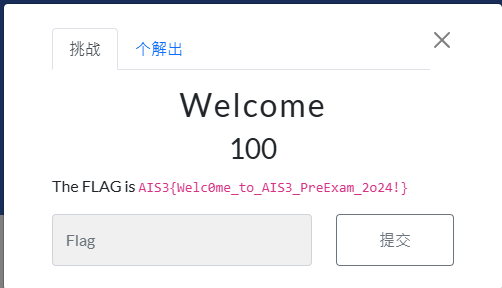
秒解,flag就在圖片上
Quantum Nim Heist
看似複雜的小遊戲,玩著玩著就手殘按到兩次,就有解了
一進去遊戲長這樣
要一掉石頭就輸入0然後再輸入要一哪一排的石頭,再輸入要拿幾顆
我發現第一次之後一直按enter,程式就會自己一直把石頭拿掉,所以我就一直按enter,在最後一步把剩下的石頭拿掉就贏了
Three Dimensional Secret
這題給的是一個pcapng檔,用wireshark打開,發現裡面有很多SSDP、ARP、TCP等等protocol,以TCP最多,我看了一下發現TCP開始傳送資料的封包內容好像有特殊的資訊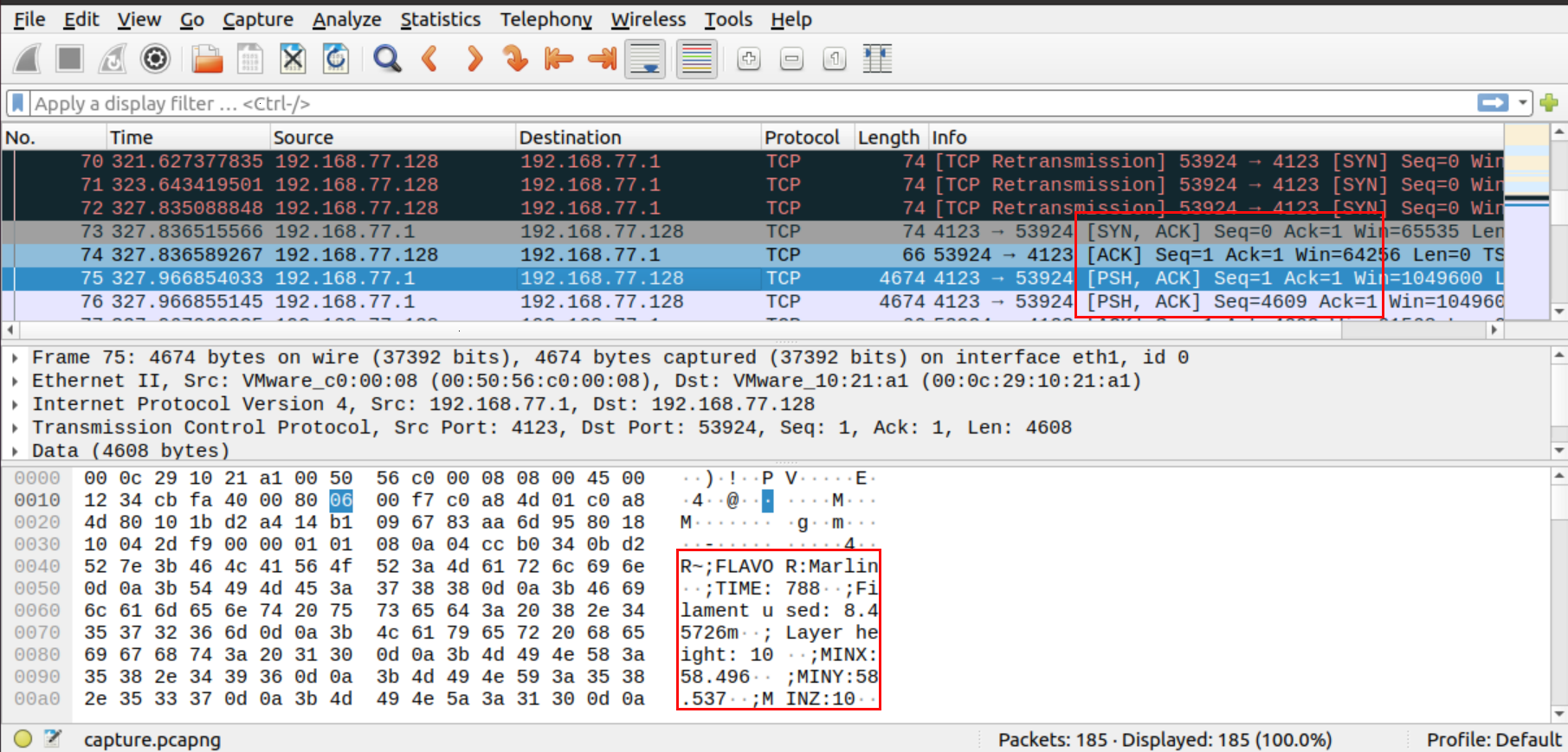
Google一下FLAVO,發現這是G-code,再找一下G-code parser,發現NC Viewer這個好線上工具,把這些封包的資訊整理出來再丟到線上的3D模擬器,就可以看到flag了
Emoji Console
這題超好玩,一開始看到這個畫面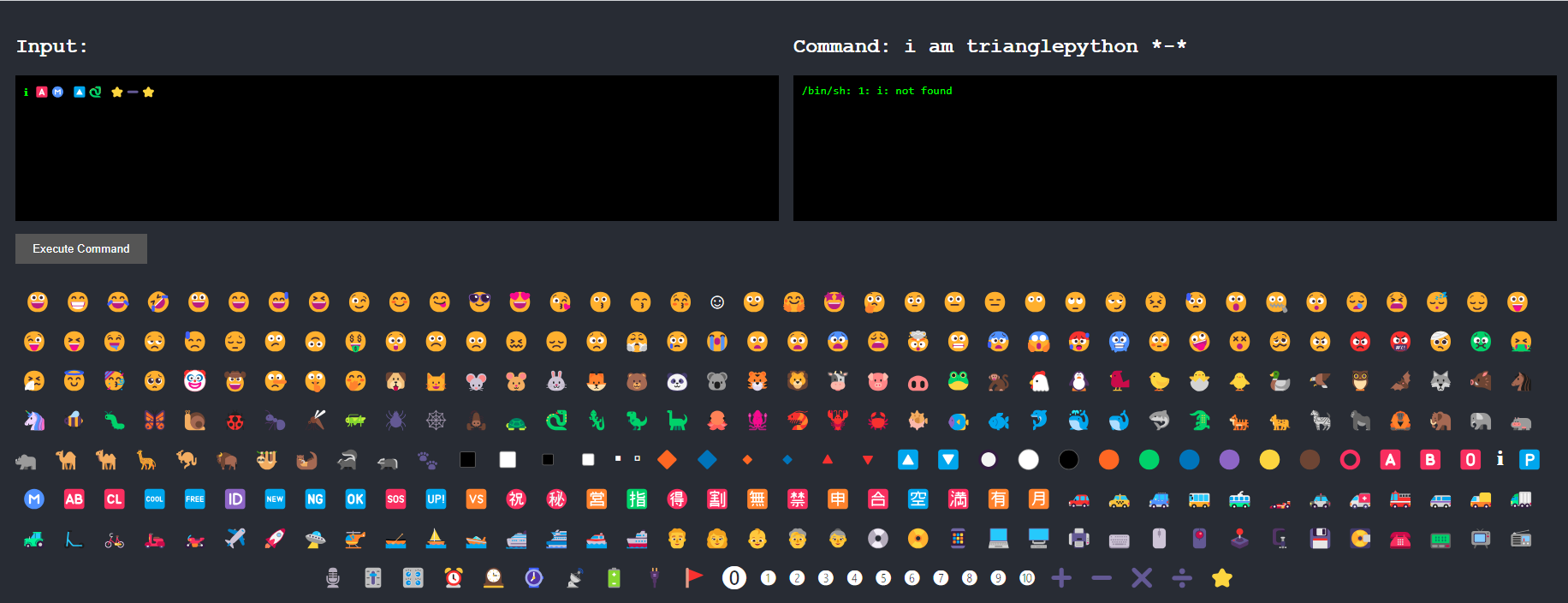
用表情符號拿到flag真的不是件容易的事,一開始的想法是cat flag,結果flag是一個資料夾…
之後我無聊試試看cat *,就拿到原始碼還有表情符號的對應,完全在意料之外
1 |
|
發現好像沒辦法繞過檢查,只好慢慢通靈,這題考驗你截斷shell指令的技巧,可以用; | && ||等等符號,但這些能用的應該不多
表情符號裡有分號的有: ‘;P’, ‘;/‘, 和 ‘;)’
有pipe的: ‘:|’
想了想之後,我就用💿 🚩😓😑🐱 ⭐得知原來flag裡面有一個flag-printer.py,再用💿 🚩😓😑 🐍❸ ⭐執行它拿到flag。原始指令是cd flag;/:|python3 *
Pipe不會管前面的指令有沒有成功完成,還是會執行後面的指令
Web
Evil Calculator
直接上原碼
1 | from flask import Flask, request, jsonify, render_template |
程式把request去掉空格和底線之後拿去eval,所以用import os或__import__(‘os’)應該是行不通,但其實可以直接open(‘flag’).read()就拿到flag
1 | curl -X POST http://chals1.ais3.org:5001/calculate -d '{"expression":"open(\"/flag\").read()"}' -H 'Content-Type: application/json' |
Ebook Parser
1 |
|
這題可以上傳epub檔案,我對epub完全不熟,去問chat gpt這到底是啥,結果發現是電子書的格式,是用xml寫的。
我其實也對xml的弱點超級不熟,google了一下有xxe可以試試看,我的payload長這樣
1 |
|
因為ebookmeta這個套件在author_list_to_string()的時候會去解析xml content裡面的creator欄位,把xxe entity塞到creator裡面,就可以觸發xxe拿到flag了
下面這個是epub的directory structure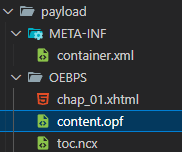
這個directory structure是請gpt幫我生的哈哈哈
這題我很驚訝可以解出來,一堆完全不熟的東西
Rev
The Long Print
題目執行會長這樣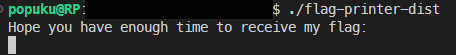
用gdb看一下main
1 | gdb-peda$ disas main |
發現main+135的地方有個sleep的call,main+130的地方把0x3674放進edi,難怪等半天都等不到flag,所以我用hexed.it把0x3674改成0x0000,再下載下來執行,發現會被蓋掉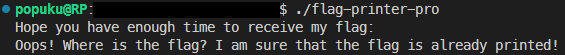
那就再改一次,把main+217的puts call改成5個nop(0x90)就可以了